Click Here to register for our upcoming event - AI Profit and Growth Briefing - with Ron Hix!
Let's Discuss How AI Can Help Your Company:
We’ve never been known as big talkers
And We Think that’s a Good Thing. At VALENTURE, We Prefer to Let The Results of Our Networking & Cybersecurity Services Speak for Us.
AI & Cybersecurity expertise
The VALENTURE Approach
AI for Real Results
We help business leaders move beyond AI hype by identifying practical, high-impact opportunities. From workflow automation to data analysis, our team helps you roll out AI tools that are effective, focused, and aligned to your goals.
Operational AI Strategy
We bring clarity to AI adoption by helping teams define where and how AI fits into their workflows. We support everything from prompt engineering to performance reviews, ensuring AI becomes usable, measurable, and repeatable across the business.
Flexible Partnership Models
We adapt to the way you want to work. Whether you need a full-service provider, a co-managed partner through CMPP, or support for one-time projects and hardware procurement, we build solutions around your business goals.
Cybersecurity-First Mindset
As a veteran-owned MSP, we focus on cybersecurity from the beginning of every engagement. If protection is not built into your foundation, your business is at risk. We prioritize defense in everything we do, including infrastructure and operations.

Securing Your Business
What You Need to Know
In today's digital world, your business is just one click away from disaster. While most organizations throw money at cybersecurity, they remain shockingly vulnerable – sometimes even more exposed than if they'd done nothing at all.
This no-nonsense guide shows you:
The Co-Managed Partner Program (CMPP)
AI Is Your Offense, Cybersecurity Is Your Defense. We Harness AI To Help You Build on a Smarter, Stronger Foundation.
AI Enablement Training
Equip teams with the skills to use AI effectively in real business scenarios. We offer role-based training that helps staff identify where and how AI can improve their day-to-day work.
AI Adoption Strategy
We bring structure to AI rollouts by aligning tools with specific business outcomes. Our process covers use case planning, policy development, and clear success metrics.
AI Process Engineering
We help you redesign manual processes using trusted AI platforms. This unlocks new levels of speed, consistency, and scalability in every department at your business.
Private AI Deployment
Our team supports secure, private AI environments tailored to your industry. This enables safer usage of AI without risking exposure to public models.
AI Lifecycle Oversight
We manage vendor relationships, tool performance, and platform compliance across your AI ecosystem. You stay focused on outcomes while we handle the complexity.
Operational AI Governance
We set up responsible use policies and performance reviews that guide AI usage over time. This protects your investment and keeps adoption aligned with evolving goals.
AI-Driven Reporting
We replace static, time-consuming reports with AI-generated insights delivered in real time. This enables faster decision-making with better visibility across your operations.
Cybersecurity Program Leadership
We build and maintain a security foundation that keeps your business protected while AI expands your capabilities. Our approach ensures risk is managed at every level.
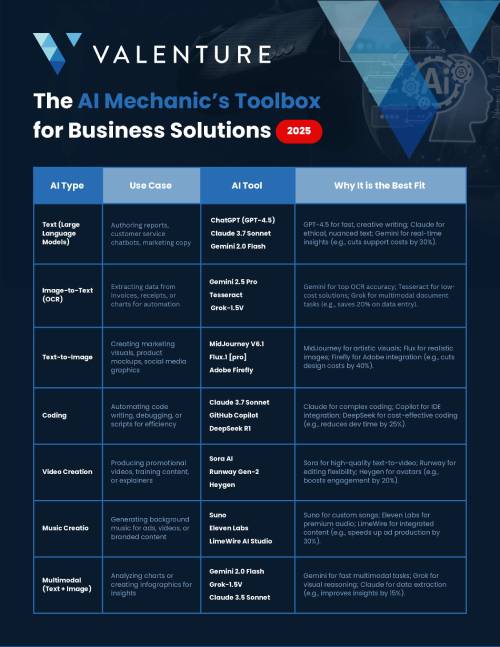
Supercharge Your Business with AI: Download The AI Mechanic’s Toolbox for Business Solutions 2025
Looking to streamline operations, enhance marketing, and boost productivity with AI?
The AI Mechanic’s Toolbox for Business Solutions 2025 is your go-to guide to the most effective AI tools across key business functions, from writing and design to coding, video, and data analysis.
Inside you’ll discover:
Download your free copy now and start transforming your workflows with AI!

Unlock AI-Driven Profit and Growth
Artificial Intelligence is reshaping how businesses grow and compete. Valenture’s AI Profit & Growth Briefing helps leaders turn AI from a risk into a revenue driver. Gain practical insights on reducing costs, accelerating decision-making, and securing your digital operations.
Learn how to implement AI with confidence and impact. Book your call and start using AI to power smarter, more profitable growth.
Our Services
CMPP Profit
Unlock profit and performance with a smarter approach to IT. CMPP Profit is Valenture’s AI-powered support program for growing businesses. We help clients automate processes, reduce overhead, and accelerate decisions using secure, focused AI tools. From productivity training to risk oversight, this managed service is designed to fuel growth while keeping your business protected.
CMPP Health
Healthcare organizations face unique pressures. CMPP Health combines AI enablement with cybersecurity and compliance to support clinical, operational, and IT leaders. We help reduce manual workloads, speed up reporting, and protect sensitive data with tailored support for PII handling, HIPAA alignment, and medical system integration. You get fewer risks, faster care delivery, and better visibility.
IT Projects
You do not have to be in our support program to benefit from our expertise. Valenture leads IT projects with clarity, structure, and a strong business case behind every decision. From cloud migrations to security stack upgrades, we manage timelines, vendors and budgets, so you do not have to. We focus on outcomes that move your business forward.
Hardware Services
The right hardware should support your business, not slow it down. We help you select, purchase, install, configure, and secure the enterprise-grade equipment you need. Whether it is network gear, firewalls, or endpoint devices, we ensure it fits into your strategy and performs as expected from day one. You get real value, not shelfware.
THE RIGHT
People
THE RIGHT
Tools
THE RIGHT
Actions
Business
Growth
The Right People + The Right Tools + The Right Actions = Secured Networks
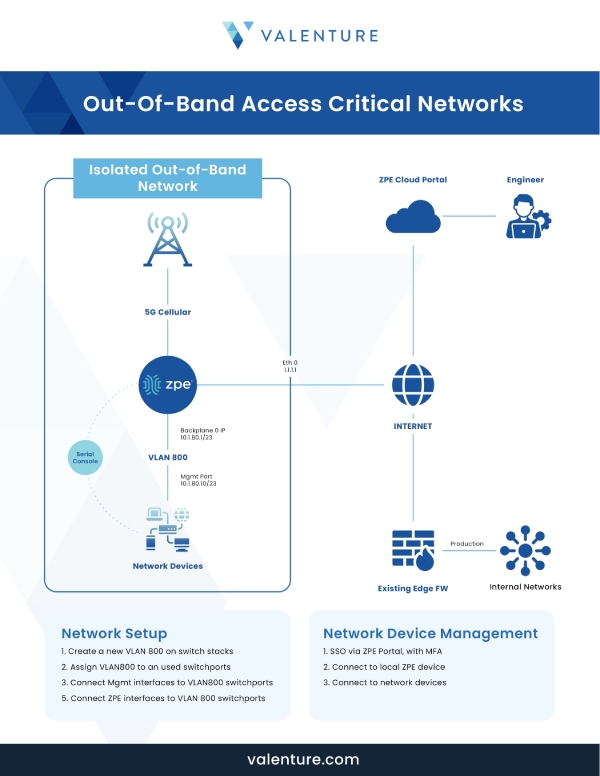
Unlock Expert Insights on Out-of-Band Management
Ensure uninterrupted access and control over your IT infrastructure, even when your network is down. Our expert guide on Out-of-Band Management reveals how to enhance resilience, security, and efficiency in remote device management.
Download this free PDF to discover:
Ready to Get Started?
Here's How It Works:
01
SCHEDULE YOUR INTRO CALL TO DISCUSS YOUR NEEDS
02
RECEIVE DETAILED STATEMENT OF WORK AND CLEAR QUOTE
03
wE SECURE YOUR NETWORK
Harness AI to Drive Profit and Improve Performance
AI is not just another tool. It can become a business advantage when applied with purpose and expertise. Valenture helps you lead with AI by aligning it to your goals, securing it from day one, and turning it into measurable business results.
Call (224) 231-0303 today or click the button below to talk to our team. Let us show you where AI fits in your business.