Have CTO’s really looked into the comprehensive impact a cyberattack has on their organization? Do the general assumptions of the cost create a clear picture of the actual impact of a cyberattack from the initial incident to full recovery?

Source: Deloitte
But what does a cyberattack really cost?
The effect of a cyberattack can carry on for years and negatively impact an organization's reputation, customer retention, the ability to operate at full capacity, and loss of proprietary information.
The short term impact of lost personal identifiable information (PII), personal health information (PHI), legal fees and regulatory fines, are generally well understood, but that typical only accounts for 40% of the total cost.
Regulatory fines, public relations costs, breach notification and protection costs, and other short-term consequences of large-scale data breaches are only the beginning. The effects of a cyberattack can ripple for years, resulting in a wide range of “hidden” costs—many of which are intangible impacts tied to reputation damage, operational disruption, or loss of proprietary information or other strategic assets.
In this article we are sharing Valenture’s decades of experience with cybersecurity attacks, from the initial attack to full recovery.
277 Days | $9.44M | $4.54M | $5.12M |
In 2022, it took an average of 277 days (9 months) —to identify and contain a breach | Average cost of a data breach in the United States | Average cost of a ransomware attack | Average cost of a destructive attack |
Source: IBM Cost of a data breach 2022
Understanding The Impact Of A Cyberattack
Impact | Consequence |
Attack investigation |
|
Regulatory compliance |
|
Devalued customer trust and brand name |
|
Operational disruption or destruction |
|
Lost revenue |
|
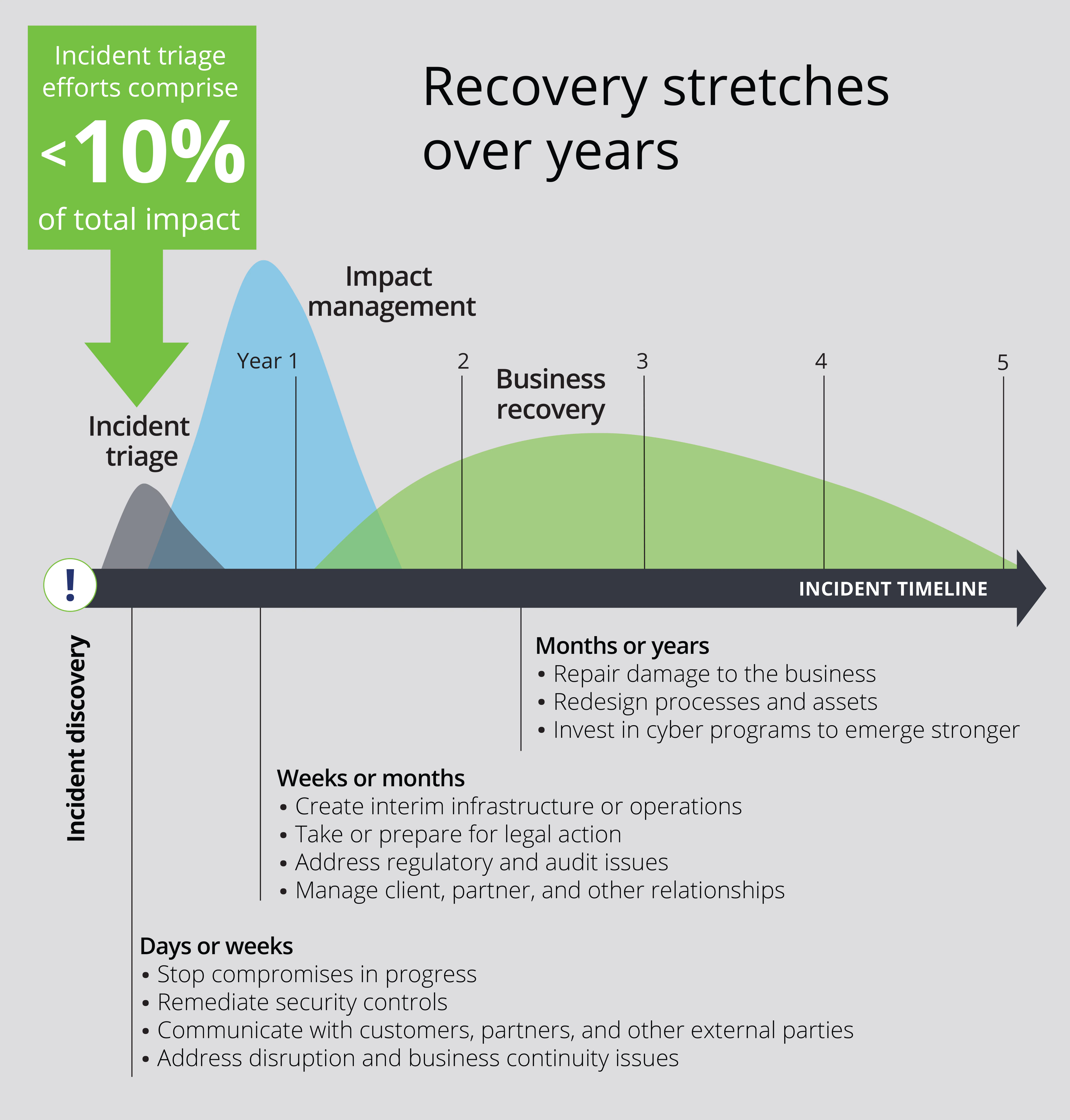
Cyberattack response lifecycle
After the initial cyberattack there is an impact remediation, and recovery stage. These stages typically involve management in almost every department of the organization in an effort to reestablish the impacted business operations. The goal for management is to define a strategy for improving cybersecurity and the level of investment needed, how to manage relationships with customers, partners, and government agencies, legal proceedings, and necessary changes to the company’s overall strategic course.
Source: Deloitte
1. Cybersecurity Incident - Immediate Impact
Impact Period: Following Days or Weeks After Security Breach Incident
Cyberattack incident are the days and weeks that follow after the cyberattack has been discovered. At this stage companies are busy with urgent decisions and activities related to communicating with customers and partners as well as defining a strategy for how to continue operations.
There is a tight focus on assessment and analysis of the impact caused by the attack, and the immediate actions that need to be taken to stop security compromises and establish temporary security control.
Cost Examples:
Diversion of key resources to handle communications with customers, partners, and other external parties.
The IT department will be fully engaged with damage control and re-establishing temporary security controls and assessing the impact.
External network security consultants may be called upon to help make the analysis and assessment before defining a roadmap for establishing temporary security controls.
2. Impact Remediation - Mid term
Impact Period: Following Weeks or Months After Security Breach Incident
In the weeks and months following a cyberattack the company’s focus is on impact remediation which means reducing the direct impact of the attack. Depending on the type of attack remediation projects can vary between establishing temporary network infrastructure and making changes to operational processes such as reducing impact to customer and partner relationships, implementation of findings in cyber assessment and audit, and responding to legal proceedings.
3. Recovery - Long Term
In the months and years following the attack, focus will increase on repairing damage to business operational processes and investing in network security that helps defend against future cyberattacks. Depending on the type of attack the recovery projects can include redesign of the network for higher security, rebuilding operational processes, systems, applications, and changing hardware.
In parallel, the business will be working on rebuilding revenue streams, reputation, and building a cyberattack detection, response and recovery process that ensures the future integrity of the business.
AI and automation offers big cost savings
Organizations that had a fully deployed AI and automation program were able to identify and contain a breach 28 days faster than those that didn’t, saving millions in costs. However, it’s not all or nothing. Organizations with a partially deployed AI and automation program fared significantly better than those without.
Valenture’s security solution employs a combination of AI, automation, and a 24/7 staffed security operations center (SOC) to maximize effectiveness.
Threats and suspicious behavior are detected early through correlation of several information sources throughout the environment. Response is automated based on runbooks crafted to each client’s specific business needs.
This combination of technology and security expertise means our clients are never unguarded and threats are mitigated as quickly as possible before damage can be done.

Get Unbeatable Cybersecurity
Valenture helps organizations create a risk-focused secure network that covers both cloud and on-location security services, to become resilient, and gain greater confidence in your ability to thrive, even in the face of a cyber crisis.
ARTICLES WORTH READING
Get Unbeatable Cybersecurity Without Breaking The Bank
Achieving excellence in cybersecurity doesn’t mean you have to hire and invest large amounts in resources, skills, and software tools. In fact, most businesses already have security tools included in their license packages, but struggle with scarcity in resources, expertise, and therefore don't make the prioritization of cybersecurity over other more “pressing” business needs.
Hybrid Network Security
Often businesses are running servers that host custom applications like email servers, custom applications etc., and will therefore need a hybrid network security solution. In such cases you will need both a SASE and SD-WAN network security solution, also known as hybrid network security.
